
GetApp offers objective, independent research and verified user reviews. We may earn a referral fee when you visit a vendor through our links.
Our commitment
Independent research methodology
Our researchers use a mix of verified reviews, independent research, and objective methodologies to bring you selection and ranking information you can trust. While we may earn a referral fee when you visit a provider through our links or speak to an advisor, this has no influence on our research or methodology.
Verified user reviews
GetApp maintains a proprietary database of millions of in-depth, verified user reviews across thousands of products in hundreds of software categories. Our data scientists apply advanced modeling techniques to identify key insights about products based on those reviews. We may also share aggregated ratings and select excerpts from those reviews throughout our site.
Our human moderators verify that reviewers are real people and that reviews are authentic. They use leading tech to analyze text quality and to detect plagiarism and generative AI.
How GetApp ensures transparency
GetApp lists all providers across its website—not just those that pay us—so that users can make informed purchase decisions. GetApp is free for users. Software providers pay us for sponsored profiles to receive web traffic and sales opportunities. Sponsored profiles include a link-out icon that takes users to the provider’s website.
4 ways to adopt a new IT security system in 2025, against technological and talent gaps
IT security software users expect struggles with technological implementation and talent sourcing in 2025. Learn how to overcome these issues when applying a new software system.

IT security software buyers are re-emphasizing their focus on cybersecurity investments for 2025. However, many anticipate operational challenges in the year ahead with implementing new technologies and sourcing talent. These were some of the core findings of GetApp’s 2025 Tech Trends Survey, which surveyed 3,276 business decision-makers in nine countries who already use or have adopted IT security software in the last twelve months for temporary or permanent use.*
Security software for IT systems encompasses various tools such as network monitoring software, access governance, encryption, and other essential systems that can protect hardware, data, and networks. These tools are essential to ensure secure operations and safeguard sensitive company information. However, firms need to make sure that their staff’s technical skills and operational hardware match the complexity of the security technology being adopted. Yet, concerns are rising about firms’ ability to manage that tech and source the talent necessary.
To help you keep up with technological trends and potential challenges expected next year, we have analyzed our data and identified four tips software buyers can use to simplify and maximize the effectiveness of their search for a new IT security system.
Key insights
38% of IT security users and adoptees are prioritizing further cybersecurity investment in 2025
Implementing technologies (37%), sourcing talent (37%), and cybersecurity threats (36%) are the three biggest challenges business decision-makers expect to face in 2025
61% say technological advancements present the biggest external challenge to firms in the next 12 months
40% say security concerns are their biggest challenges when planning an investment in a new IT security system
Industries are making cybersecurity their biggest priority in 2025
Despite already having an effective IT security software system, many businesses are considering increasing investments in cybersecurity. This may be for a variety of reasons, such as upgrading existing systems, putting strong protections in place, compatibility issues, or due to switching providers in the coming twelve months.
In total, 38% of IT security users will prioritize cybersecurity investment next year. A crucial factor explaining this trend is the need to secure essential and sensitive data that companies manage.
It’s no great surprise that the industries prioritizing cybersecurity in 2025 have some of the most sensitive data in their possession or represent the biggest targets for hackers. For example, the top five sectors most likely to prioritize cybersecurity in their budget for next year include:
IT - 56%
Government and NGO - 38%
Manufacturing & construction - 38%
Finance (financial services and insurance) - 37%
Retail - 37%
However, the picture shifts slightly when looking at adoptees of IT security software during 2024. In this situation, we found that adoption was a tendency in industries with more complex network infrastructures or with the most advanced digital operations systems, as the graph below demonstrates.
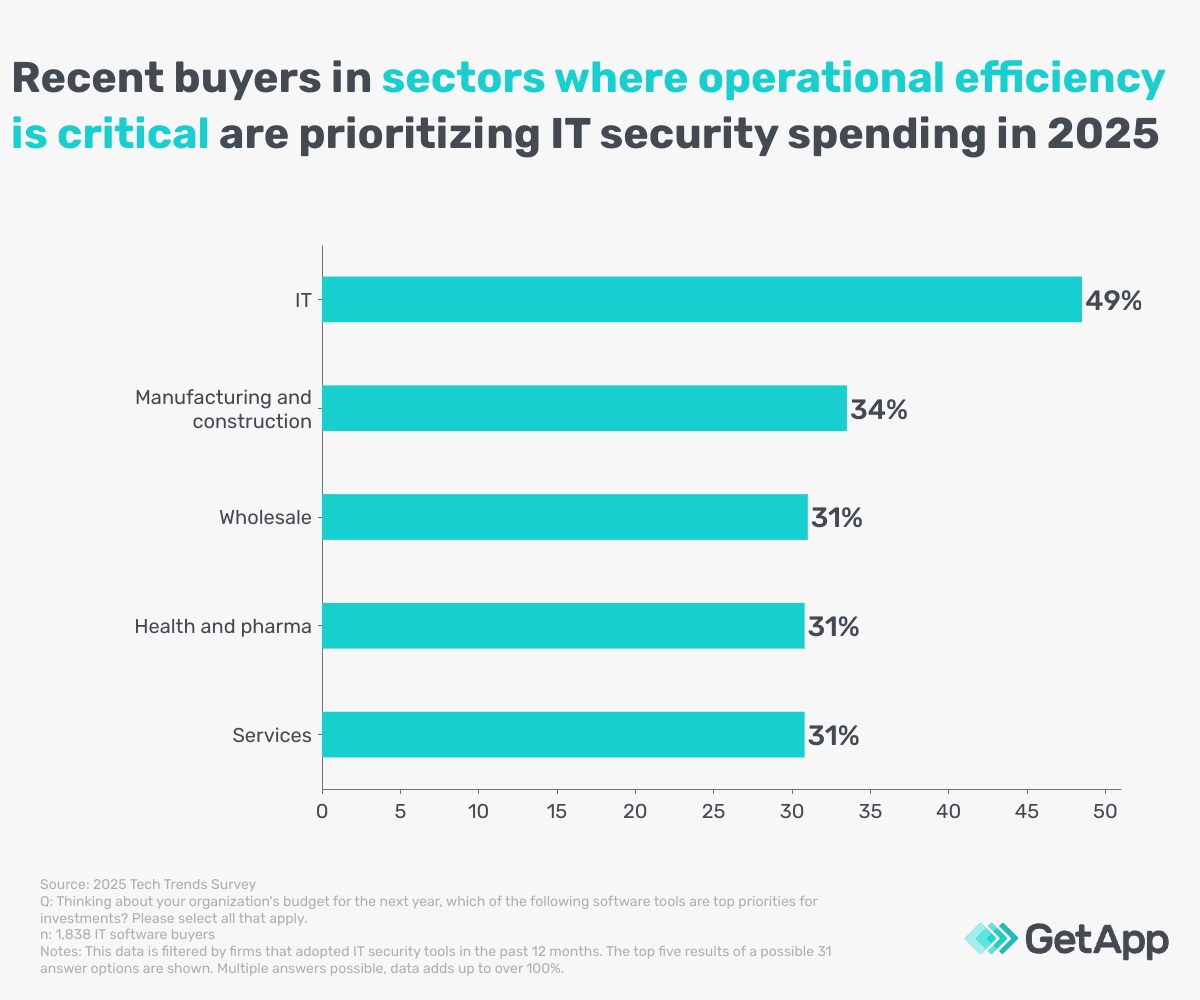
The trend for businesses with extensive digital infrastructure to prioritize IT security systems may be a response to stories of recent ransomware attacks on organizations of a similar nature. There have been many news reports during the last 12-18 months, especially in the medical sector. [1] This is likely driving some of the momentum in these sectors, where reliance on smooth processes and the ability to access complex and sensitive personal data is most crucial.
There are good reasons to try and get out ahead of attacks such as ransomware. In GetApp’s 2024 Data Security Survey, we also saw that ransom attacks are still causing headaches for many firms, with 44% of IT professionals reporting one or more incidents at work in the past year. There are also major concerns that AI-enhanced attacks will make ransomware incidents more prevalent.
Keeping network administrators vigilant
Network monitoring is an especially important means of controlling security. This software assists with overseeing network hardware and tools but can crucially provide early warnings when irregular traffic or unauthorized access makes its way onto the system. It can also identify where technology needs upgrading or more management effort.
Implementation and technical expertise are among the biggest challenges expected next year
Challenges arising are a reality of being in business, which is why it’s important to try and look for opportunities to get ahead of potential issues. We looked at how firms are approaching this task going into 2025 and what trends could be the focus in the year ahead.
Some of the top business concerns that IT security users identify are issues related to implementing technologies, sourcing qualified talent, and cybersecurity threats.

Many of these concerns revolve around issues with having the right skills and technological capacity within a business. Therefore, it is no surprise that 61% of IT security users identify technological advancements as one of the biggest external factors expected to challenge businesses in 2025.
This is expected to affect a number of industries more profoundly than others too. Amongst all participants surveyed for this study, members of the following sectors were most likely to select technological advancements as the biggest externalized issue for 2025:
IT - 70%
Marketing and communication (marketing/advertising, entertainment/media, and telecommunications) - 64%
Finance (financial services and insurance) - 62%
Education - 61%
Real estate - 58%
4 tips to simplify the process of selecting the most suitable IT security software
Selecting an IT security software system is not necessarily a fast process, but it must be conducted decisively to get results at the right time. Based on our findings, companies are expecting difficulties adapting to technological evolution. To help simplify things, we’ve highlighted four insights from our data that businesses can use to make the process smoother.
Plan around common software buying chokepoints
The software buying process needs to be carefully planned to address potential pain points at the time of system implementation. Our data shows that for IT security users, many of the more general business challenges seen before also impact software buying to a degree.
The most common challenges identified that organizations using IT security software face when adopting new investments in software include:
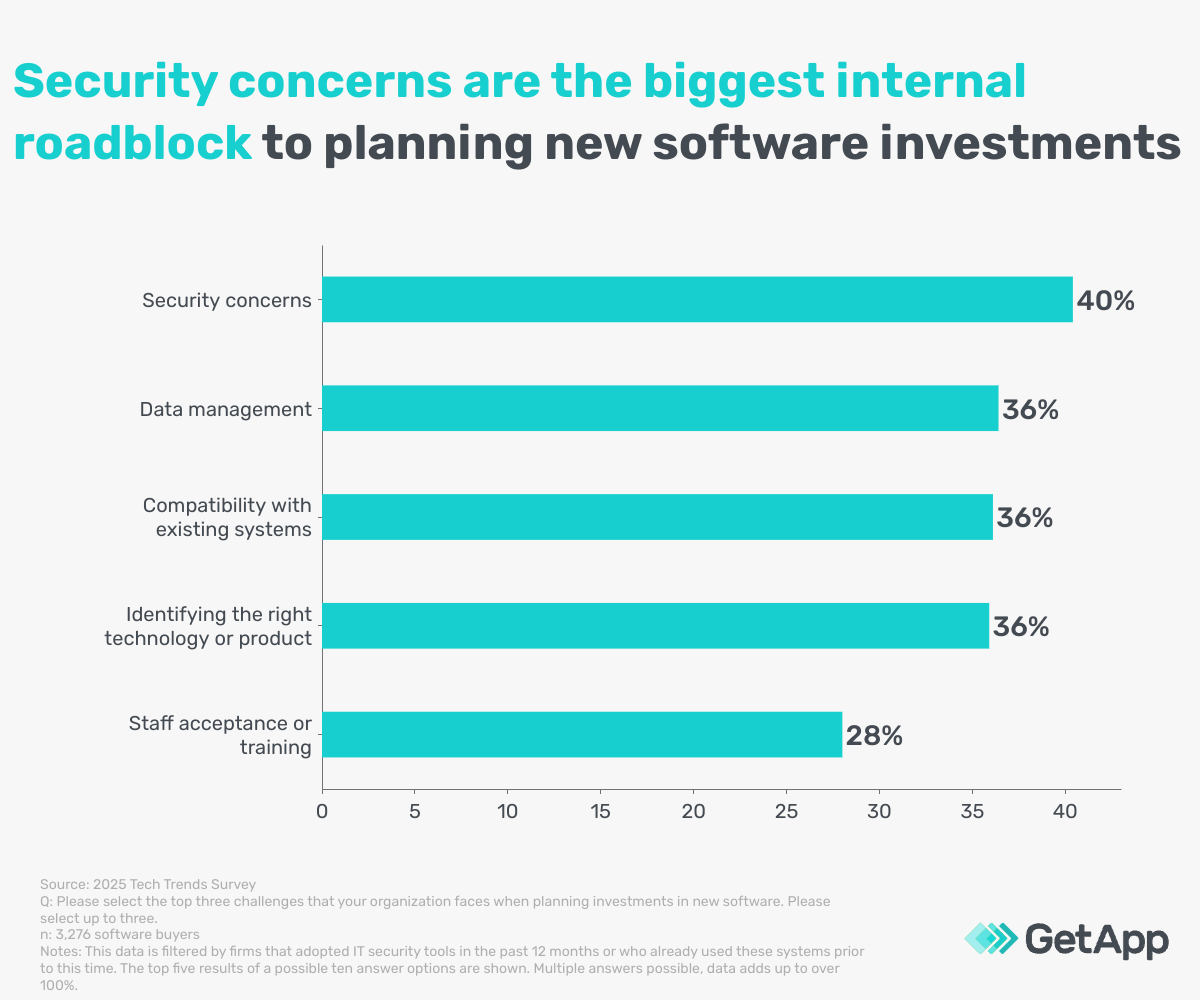
These offer an important starting point when planning your next purchase. Since these are the top factors that can hinder an investment, it is important to address these core concerns from the start.
To overcome the top issues such as security concerns and data management, it is essential to consider systems that have robust protections with decent encryption protocols, regular updates to protect against new threats, and control access management effectively.
Create an initial list of vendors based on reputation and hands-on experience
There are hundreds of software platforms for a buyer to choose from. For example, on GetApp we list over 500 cybersecurity vendors, however, there are even more offering IT security software on the market. Narrowing the choices is, therefore, the next logical step of a software buying journey.
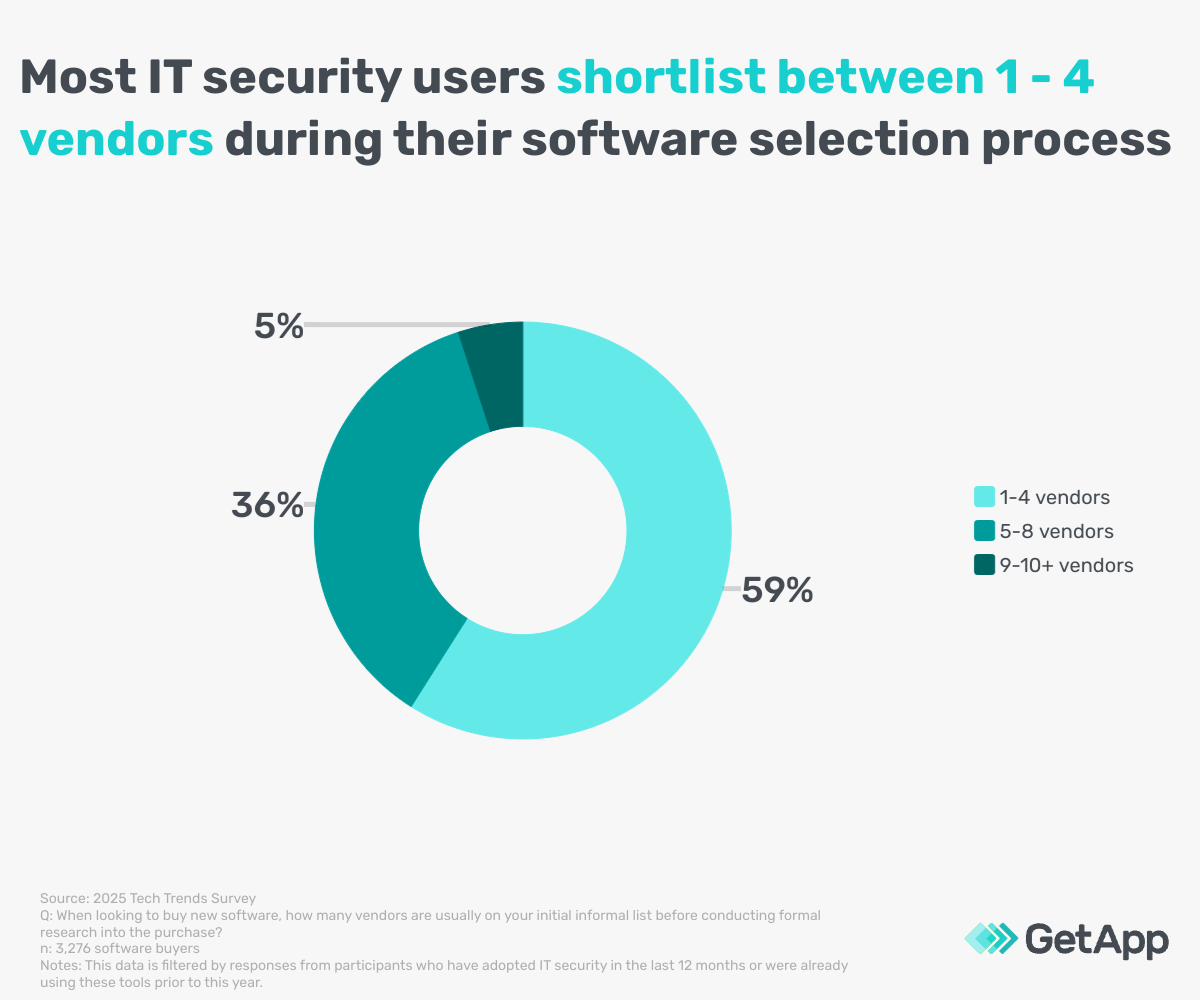
We found that during the purchasing process, IT security users mostly work with an initial list of 1-4 possible options. However, over a quarter (28%) will consider 5-6 vendors ahead of formal research.
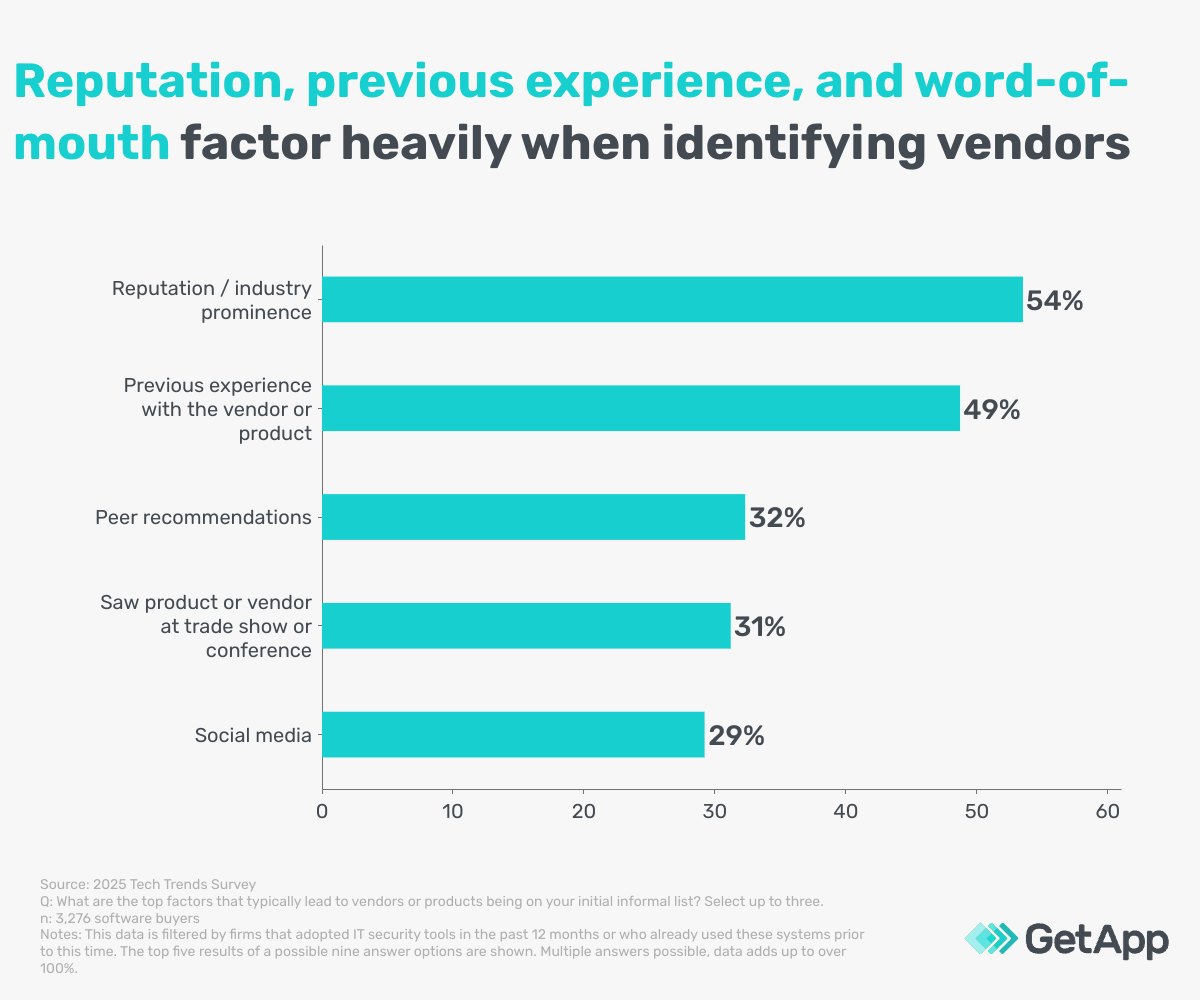
The list is very often informed by options with high reputational and industry prominence. Over half (54%) use this criterion to make their initial list. However, experience and recommendations also feature prominently, with many amongst our sample using these to guide their decision.
Refine the list of options with reviews
Our data also shows the importance of using customer reviews to refine an initial list of software providers. Of our sample, 41% of IT security users regard these as the most influential source of information when conducting formal research into the available options, which was the most selected option above other considerations like recommendations from industry experts (40%) and Google searches (38%).
It is worth noting that currently, Google searches for software carry their own security risks as reports show malicious ads encouraging users to download unsafe applications remain a common issue. [2] Therefore caution is needed when using this approach.
Comparison and review sites can prove especially effective when assessing relative customer satisfaction from previous buyers. Among IT security software users 58% trust review sites to assess user satisfaction over the reviews featured on vendor websites.
Avoid dissatisfaction by trying before buying
It’s hard to know if a software tool works as you need it to without trying it first. It is, therefore, vital to test an IT security platform before making the final selection from your final shortlist to ensure it works as expected.
A software tool that doesn’t fit the company’s needs is a major reason for regret in an IT security software purchase. Aside from causes, such as higher-than-expected expenses, accounting for dissatisfaction among 32% of IT security users, a top issue for regretful buyers was that they found the software either too basic (31%) or too complex (30%) for their business needs after committing to the purchase.
There are many ways to get a hands-on view of the system you’re considering before making the final decision. For example, buyers can take advantage of free trials, free versions, or operational demonstrations offered by many IT security vendors on the market. This proves influential in the decision-making of many in our sample, too. We found that 62% of IT security users get a product trial before buying, whilst 54% get an online demonstration.
Optimizing the IT security buyer’s journey
Under perfect conditions, an IT security buying process can be carried out calmly and in the time necessary to make the ideal choice. However, business pressures don’t always allow for that, especially as firms increasingly try to keep up with technological evolution and a new generation of cyberthreats in the months ahead.
Whilst the perfect situation doesn’t always exist, it is important to look at ways to build expectations of what the IT security software process involves, to help stakeholders plan the steps needed, and to build confidence in the process.
Survey methodology
*GetApp’s 2025 Tech Trends Survey was conducted online in August 2024 among 3,276 respondents in the U.S. (n=658), U.K. (n=333), Canada (n=323), Australia (n=336), France (n=322), India (n=343), Germany (n=331), Brazil (n=325), and Japan (n=305), at businesses across multiple industries and company sizes (5 or more employees). The survey was designed to understand the timeline, organizational challenges, adoption & budget, vendor research behaviors, ROI expectations, and satisfaction levels for software buyers. Respondents were screened to ensure their involvement in business software purchasing decisions and that they use IT security software.
Sources:
A third of Americans could have had data stolen in big health care hack, CNN Politics
Using Google Search to Find Software Can Be Risky, Krebs on Security

David’s research and analysis is informed by more than 150,000 authentic user reviews on GetApp and nearly 3,000 interactions between GetApp software advisors and software buyers.
His thought leadership work has been featured in TechRadar, Startups Magazine, and Raconteur.

