
GetApp offers objective, independent research and verified user reviews. We may earn a referral fee when you visit a vendor through our links.
Our commitment
Independent research methodology
Our researchers use a mix of verified reviews, independent research, and objective methodologies to bring you selection and ranking information you can trust. While we may earn a referral fee when you visit a provider through our links or speak to an advisor, this has no influence on our research or methodology.
Verified user reviews
GetApp maintains a proprietary database of millions of in-depth, verified user reviews across thousands of products in hundreds of software categories. Our data scientists apply advanced modeling techniques to identify key insights about products based on those reviews. We may also share aggregated ratings and select excerpts from those reviews throughout our site.
Our human moderators verify that reviewers are real people and that reviews are authentic. They use leading tech to analyze text quality and to detect plagiarism and generative AI.
How GetApp ensures transparency
GetApp lists all providers across its website—not just those that pay us—so that users can make informed purchase decisions. GetApp is free for users. Software providers pay us for sponsored profiles to receive web traffic and sales opportunities. Sponsored profiles include a link-out icon that takes users to the provider’s website.
How to Prevent Business Email Compromise and Spear Phishing Attacks
Spear phishing and BEC attacks are already formidable threats. Deepfake technology will make them worse.

In the past, phishing attacks were typo-riddled emails blasted out to a mass audience, commonly offering a reward for helping a deposed monarch get his money out of the country. Conversely, today’s spear phishing emails are personalized, professionally written, and appear to come from organizations that you do business with.To make matters worse, business email compromise attacks aimed at high-value targets have skyrocketed in recent years.
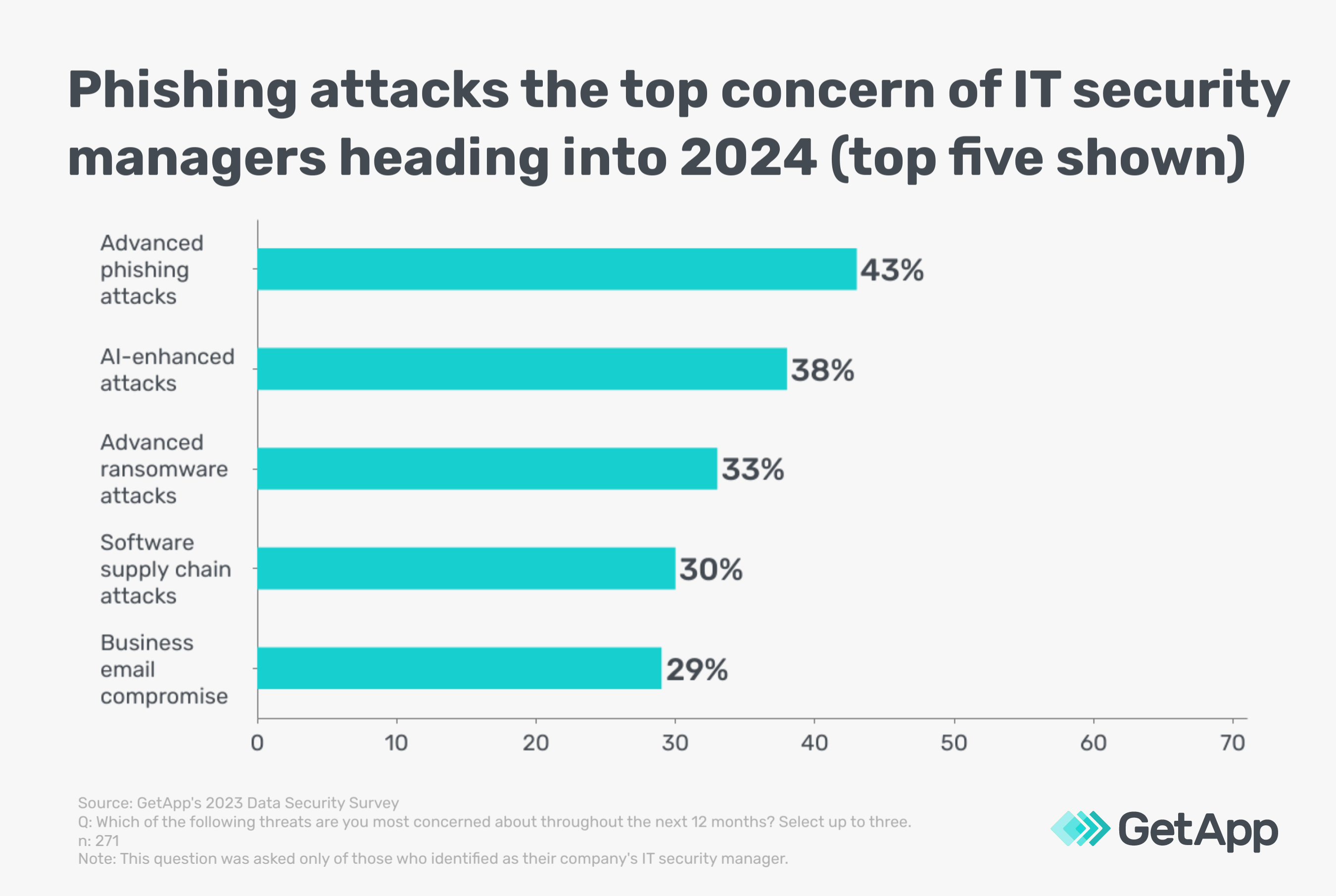
GetApp’s 2023 Data Security Survey* finds that advanced phishing attacks are the top concern of IT security managers heading into 2024, while business email compromise ranks within the top five. In this article, we’ll explain how these schemes rake in billions and what you can do to prevent them. We’ll also explore how deepfake technology is already taking these scenarios to the next level.
Spear phishing: A minor ploy with major consequences
It’s easy to let your guard down when a fraudulent email appears relevant and addresses you by name, such as a bogus password reset email. Spear phishing emails tend to impart a sense of urgency (e.g., missed payment) and request some sort of immediate action be taken. This might include clicking a link to confirm account credentials or downloading a malware-laden attachment.
It’s also important to remember that spear phishing occurs on various platforms including social media accounts and messaging apps.
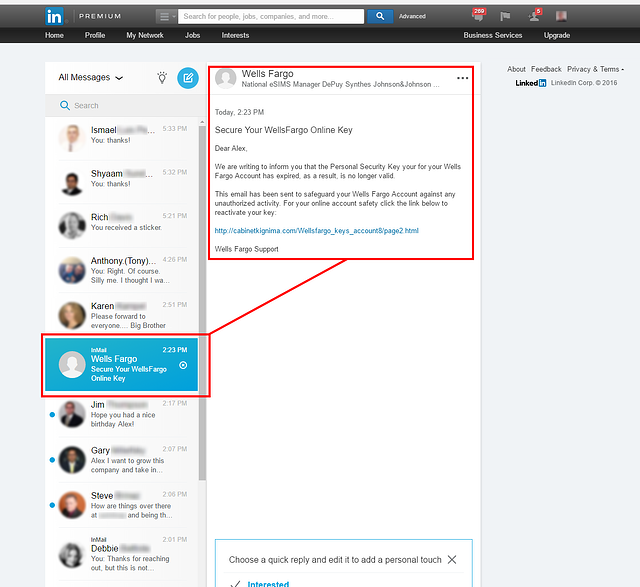
Example of a LinkedIn spear phishing message [1]
Perhaps the most consequential spear phishing attack occurred in March, 2016, during the lead up to the 2016 U.S. presidential election. John Podesta, Hillary Clinton’s campaign chairman, received an email purporting to be from Google notifying him that someone had attempted to access his email account from Ukraine. [2]
The familiar message stated “Google stopped this sign-in attempt. You should change your password immediately.” Adding to the scheme’s effectiveness, the Podesta email originated from a seemingly official-though definitely fake-googlemail.com domain.
The shortened URL contained in the spear phishing email led to a bogus phishing site that mimicked a Google password reset page. Several months after Podesta’s valid Gmail credentials were entered into a phishing website, 50,000 of his emails were leaked and the Democratic National Committee’s servers were hacked.
The rest is history.
Phishing tests are used to gauge employee susceptibility to spear phishing schemes and are an effective way to spread awareness of the attack’s effectiveness. However, GetApp's 2023 Data Security Survey found that only 63% of businesses conduct phishing tests. That’s a missed opportunity for more than one in three companies that is well worth the return on investment. Phishing tests can be designed by an internal IT team or administered by a contracted security company,
Business Email Compromise (BEC): a $50 billion dollar scheme
According to the FBI’s 2023 IC3 report, BEC schemes have cost businesses more than $50 billion over the last decade with losses increasing by 17% in 2022 alone. [3]
Also known as CEO fraud, BEC schemes target executives, senior management, or any other employees with access to highly-sensitive data or payment mechanisms. Part of the reason that BEC attacks are so costly is that they often end in a high-dollar wire transfer, payment of a fake invoice, or the transmission of payroll information.
Prior to launching BEC attacks, social engineers often research their target using online resources such as company websites, LinkedIn, and Twitter profiles. These sources tend to include job titles and departments that allow an attacker to piece together working relationships and personal dynamics within an organization. Furthermore, people commonly have personal websites that act as an online resume, providing more than enough information for a social engineer’s needs.
Email security and SPAM filtering are essential elements of IT security. However, most BEC attacks don’t breach IT security at all. Instead, they dupe employees into tossing sensitive data right over a company’s razor-tipped IT security wall. And because emails related to BEC attacks are sent only to a select few, they often slip past SPAM filters.
In an example from 2019, a Lithuanian man was extradited to the United States to face wire fraud charges resulting from a string of successful business email compromise attacks. In the end the man pleaded guilty to fleecing more than $120 million from numerous companies including an unnamed “multinational online social media company.” [4]
Deepfake technology: The next phishing frontier
Deepfake audio and video technologies convincingly mimic a person’s physical or vocal features so that they seem to be doing or saying something that never occurred in reality. And although it only recently emerged, deepfake technology is already becoming mainstreamed with apps such as Lensa AI and FaceApp. A recent viral deepfake song ostensibly featuring pop stars Drake and The Weeknd was convincing enough to initially trick fans into thinking it was authentic, showing how far deepfakes have come in a short amount of time. [5]
Deepfake technology is poised to take the spear phishing and BEC concepts to extremes. Company leaders commonly participate in conferences, panels, podcasts, interviews, and assorted other media interactions. Audio or video from these sessions combined with machine learning techniques such as Generative Adversarial Networks (GANs) can extrapolate new video or voice data from existing data.
It’s easy to envision how this technology will inevitably be used for nefarious purposes. In one example, AI-assisted voice phishing (vishing) calls that convincingly mimicked a CEO’s voice were used to convince his direct report to wire $243,000 to a bogus account. [6]
Our fundamental abilities to discern what’s real and what’s fake are clearly eroding. One factor is the mass proliferation of confusing information on the internet. A more important factor is the sophistication of one’s digital media literacy in understanding how easily photos can be doctored, voices simulated, and faces swapped. Social engineering techniques are about to get much more aggressive and even more effective.
Best practices to prevent spear phishing and BEC attacks
If you receive an abnormal request from a colleague or superior, follow up with them using a secondary means of communication to verify the request. If they’re in the same office, simply walk over and ask, “Did you just send an urgent request to wire $2.3 million to a new copper supplier in Bulgaria?”
Better yet, all companies should develop strict policies that require a second form of verification to authorize wire transfers and the transmission of payroll or tax records.
The following best practices can also help to prevent spear phishing , business email compromise, and other IT security threats:
Maintain unique passwords for every application and enable multi-factor authentication when available.
Refrain from clicking on embedded links in emails. Instead, navigate directly to the company's website via search or by typing its URL into a browser.
Consider the type of information you share on social media, how it can be used to discern details about your personal life, and the ways it can be leveraged.
Tighten privacy settings on social media accounts, mobile applications, web browsers, and internet-connected devices.
Research potentially deceptive URLs, email addresses, and social media usernames that could be used for deceptive purposes.
Beware of shortened URLs that conceal a hyperlink's destination.
Conduct internet searches on yourself to see what kind of information surfaces. Take a few minutes to opt-out of invasive people-search websites, such as Spokeo and Mylife.
Develop specific processes that require a second form of verification to authorize wire transfers and the transmission of payroll or tax records.
Conduct phishing tests to determine employee susceptibility to fraudulent emails.
Establish a clearly defined acceptable use policy (AUP) for internet and email use.
To learn more about preventing spear phishing and BEC schemes, read our report: Social Engineering Techniques that Hack Your Employees
Sources
1. Phishing Examples, Phishing.org
2. The phishing email that hacked the account of John Podesta, CBS News
3. Business Email Compromise: The $50 Billion Scam, Internet Crime Complaint Center (IC3)
4. Lithuanian Man Sentenced To 5 Years In Prison For Theft Of Over $120 Million In Fraudulent Business Email Compromise Scheme, U.S. Department of Justice
5. An A.I. Hit of Fake ‘Drake’ and ‘The Weeknd’ Rattles the Music World, The New York Times
6. Fraudsters Used AI to Mimic CEO’s Voice in Unusual Cybercrime Case, The Wall Street Journal
Methodology
*GetApp’s 2023 Data Security Survey was conducted in August 2023 among 872 respondents to learn more about data security practices at U.S. businesses. All respondents were screened for full-time employment at U.S. businesses. 362 respondents identified as IT management professionals and 271 identified as IT security managers.


