
GetApp offers objective, independent research and verified user reviews. We may earn a referral fee when you visit a vendor through our links.
Our commitment
Independent research methodology
Our researchers use a mix of verified reviews, independent research, and objective methodologies to bring you selection and ranking information you can trust. While we may earn a referral fee when you visit a provider through our links or speak to an advisor, this has no influence on our research or methodology.
Verified user reviews
GetApp maintains a proprietary database of millions of in-depth, verified user reviews across thousands of products in hundreds of software categories. Our data scientists apply advanced modeling techniques to identify key insights about products based on those reviews. We may also share aggregated ratings and select excerpts from those reviews throughout our site.
Our human moderators verify that reviewers are real people and that reviews are authentic. They use leading tech to analyze text quality and to detect plagiarism and generative AI.
How GetApp ensures transparency
GetApp lists all providers across its website—not just those that pay us—so that users can make informed purchase decisions. GetApp is free for users. Software providers pay us for sponsored profiles to receive web traffic and sales opportunities. Sponsored profiles include a link-out icon that takes users to the provider’s website.
Tokenization vs Encryption - Which One Is Best for SMBs?
Your business might need both tokenization and encryption. However, to make the most of these security methods, you need to understand the difference between them.

The difference between tokenization and encryption mainly lies in how they work. While both help protect business data, tokenization is specifically recommended under the Payment Card Industry Data Security Standard (PCI DSS) [1], a regulation that 49% of small businesses said they must follow, according to GetApp's 2023 IT Management Survey*.
But should small business owners opt for tokenization, especially to secure payment-related information? Is encryption not enough to protect the company’s data? We talked to Vikram Bodicherla [2], an Android engineer at WhatsApp who offers a unique perspective on both security methods.

“Though encryption and tokenization serve very different purposes, they are both likely needed for different systems/parts of a workflow. Also, tokenization is often backed by encryption.”
—Vikram Bodicherla, Android Engineer at WhatsApp
To understand their similarities and differences, we will explore tokenization and encryption separately and dive deeper into an example from Bodicherla to zero in on their different use cases.
What is tokenization?
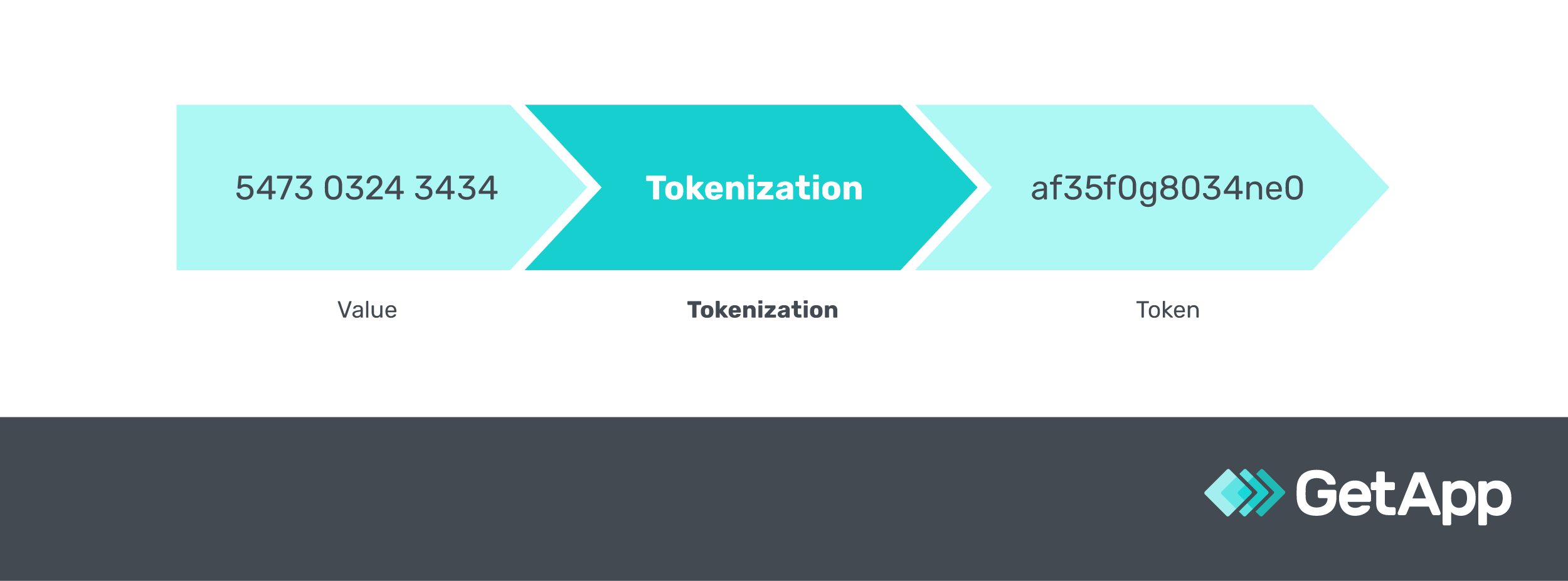
Tokenization is a way to keep important information safe from cybercriminals. It replaces the sensitive parts of data, such as credit card numbers and passwords, with random letters and numbers called tokens. These tokens are useless to anyone trying to steal them because they don’t hold any real value.
Bodicherla explains that the original, valuable data is kept in a safe place, separate from the tokens. This tokenization process, known as Data Tokenization, is a top choice for businesses, especially when following rules like PCI DSS for customer data protection.
In scenarios like online transactions, a specific form called Payment Tokenization is utilized to secure payment information. By using tokenization, businesses make it hard for cybercriminals to get their hands on valuable and real data.
4 main types of tokens for tokenization
Bodicherla says it depends on the context and the use case to decide the correct kind of tokenization for your small business.
| Type | What is it? | How it works? | Best for which business? |
|---|---|---|---|
| Cryptographic tokenization | Uses cryptographic algorithms, which are rules for making the data unreadable, to create tokens. It stores the original data in a secure data vault for reference. | It replaces the credit card number with a token generated through a cryptographic algorithm, which scrambles the data into a coded form. | Businesses with high-security needs, like banks and financial institutions, use it for its effective security to tokenize account numbers, preventing data breaches. |
| Non-cryptographic tokenization | Creates tokens without cryptographic algorithms. | It uses random number generation to generate a token that can replace the credit card number. | Small retailers or online shops use it as it’s simpler and less costly to tokenize customer payment info, ensuring a basic level of security without much complexity. |
| API-based tokenization | Uses an application programming interface (API) that communicates with an online service to create tokens. | During an online payment transaction, an API connects with a tokenization service to collect a token and store it in place of the credit card number. This helps in keeping the original data secure. | eCommerce platforms, or any business utilizing online payments, use it as it’s easy to implement and often more secure and compliant. For instance, an eCommerce platform might use a third-party tokenization service to secure customer payment data during transactions instead of building an in-house solution, which can be costly and complex. |
| Vaultless tokenization | Also uses cryptographic algorithms to create tokens but does not store the original data, reducing storage requirements and associated risks. | It swaps the credit card number with a token generated using a cryptographic algorithm. This method doesn't keep the actual card number. Instead, it makes a new token that points to the data without showing it. | Businesses with limited storage resources or those looking to minimize data storage risks, such as healthcare institutions, can use it to tokenize sensitive data like patient records, reducing the risk of data breaches without needing extensive data storage. |
What is encryption?
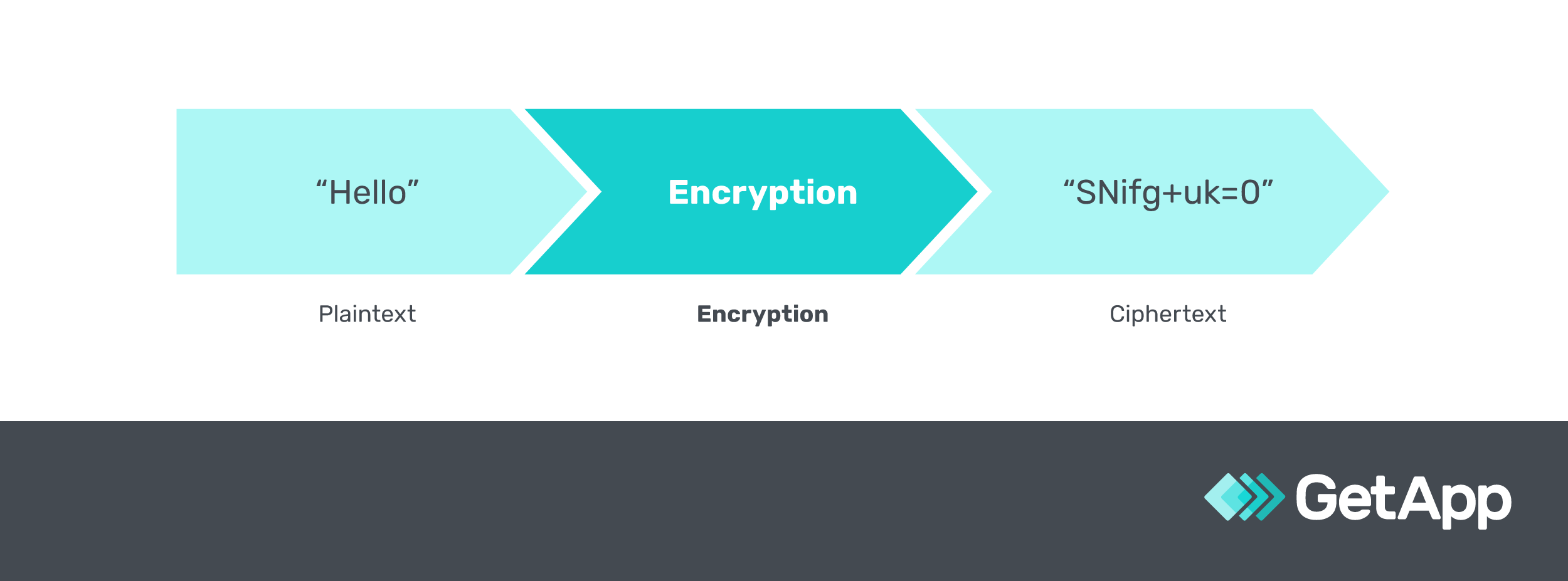
Encryption is like a secret code for keeping your data safe. It scrambles your important information into a mix of random letters and numbers called ciphertext. Only someone with the right key can unscramble the cipher back to make sense. Unlike tokenization where data is swapped for tokens, encryption changes how data looks to anyone who isn’t supposed to see it.
It’s a solid way to send sensitive information securely, like when you’re chatting on common messaging apps like Instagram or WhatsApp. Even if someone intercepts the encrypted data, they won’t understand what they have without the key to decode it. Businesses and nearly every team communication app today use data encryption to protect their data from prying eyes.
2 main types of encryption
Bodicherla discusses the two main types of encryption businesses use in day-to-day operations:
| Type | What is it? | How it works? | Best for which business? |
|---|---|---|---|
| Symmetric encryption | Uses the same key to both encrypt and decrypt data. | When you log in to a Wi-Fi network with a password, symmetric encryption is at play. The same password is used to establish a secure connection (encrypt) and to access the network (decrypt). | Businesses that need to securely share data within a closed, trusted network, like internal teams in a company, use it to keep shared files secure. |
| Asymmetric encryption (public key cryptography) | Uses a pair of keys: a public key to encrypt data and a private key to decrypt it. | When you send a secure email using a service like Gmail, it may use asymmetric encryption. Your message is locked (encrypted) with a public key, but only the recipient’s unique private key can unlock (decrypt) it. | Businesses engaging in secure communications with external entities, like customer communications or B2B transactions, use it to securely exchange data with parties outside their organization. |
Tokenization and encryption complement different systems of a workflow
Bodicherla says tokenization is often backed by encryption. To explain further, he followed with the example of a user on an eCommerce cart. When the user hits the ‘Buy’ button, various systems need different parts of the billing order—the billing system needs access to the credit card number while the inventory system needs the delivery address, but not vice-versa.
In this case, relevant parts of the order should be tokenized before sending it to different systems. By tokenizing relevant parts, you ensure that sensitive information is not exposed to systems that don't require it, reducing the risk of data leaks or breaches.
Now, say we need to store the credit card information for payment retries, etc. This data should be stored in an encrypted fashion so unintended recipients (e.g. logging systems, employees with access to the database tables, etc.) don’t have access to the credit card information. In contrast, relevant systems (e.g. the billing system) do.
If unintended recipients also have access, it could lead to misuse of credit card information, fraudulent transactions, and a severe breach of privacy, which can be catastrophic for the business and its customers.
However, there’s a lot of overlap where the actual content is replaced by the token that needs to be stored in a database. In such a case, the data stored in the database is also encrypted. This way, even if someone accesses the tokens in the database without the proper decryption key, they won't be able to revert it back to the original sensitive data, showcasing how tokenization is often backed by encryption to bolster security.
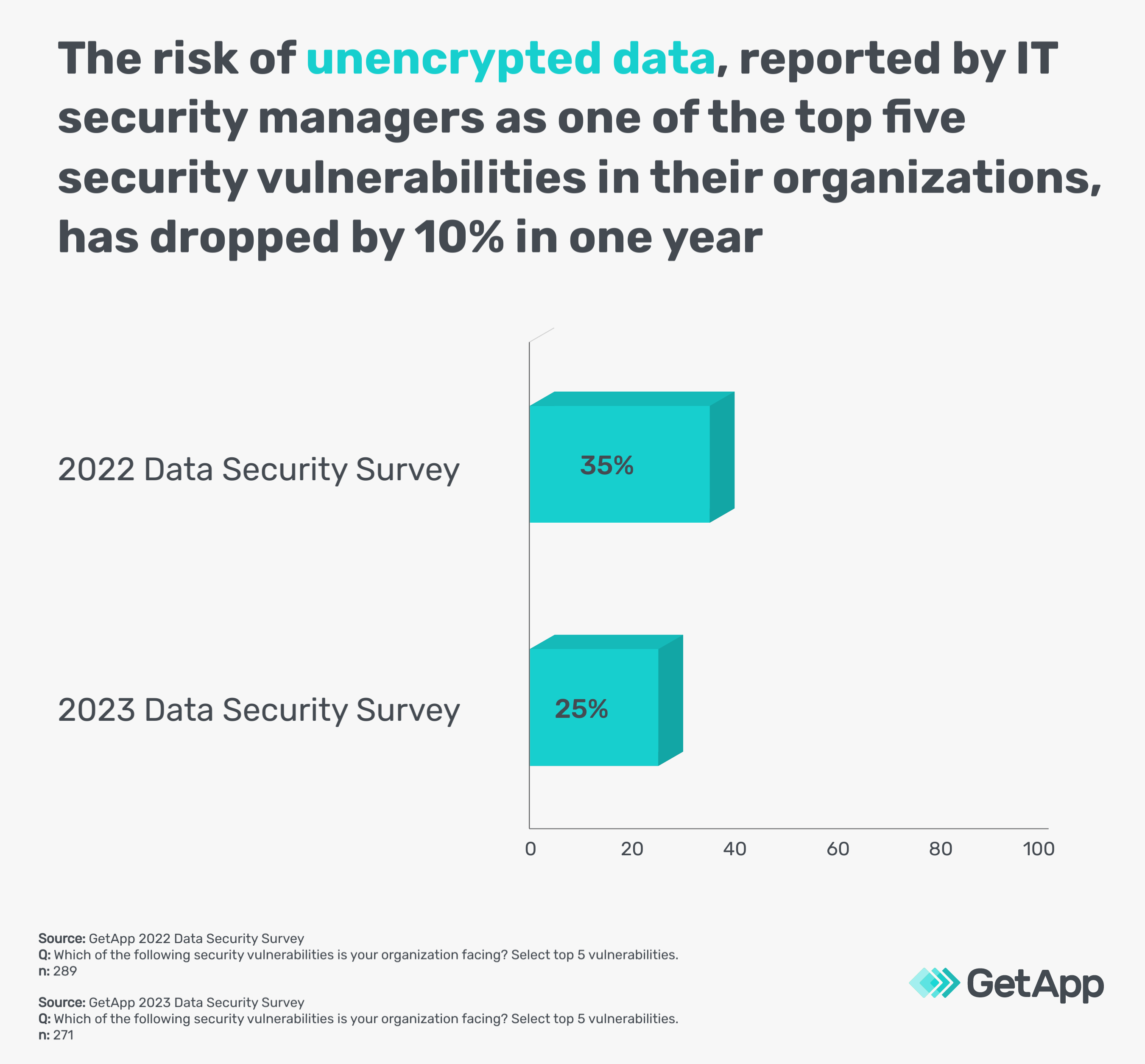
This could also be one of the reasons why the risk of unencrypted data among small businesses has been reduced according to GetApp’s 2022** and 2023 Data Security Surveys***.
Data masking vs. encryption: Both seem similar, but are different
Data masking hides certain parts of data with characters or other data, making the original data unrecognizable, but not changing it. For example, it shows only the last four digits of a phone number. On the other hand, encryption transforms data into a coded form using a key. Only someone with the correct key can change it back. So, while data masking disguises data, encryption alters it, providing a higher level of security.
Encryption vs tokenization: 6 key differences to know
Bodicherla’s insights helped us understand the distinct differences between both security measures:
1. Encryption follows a mathematical process
Bodicherla says encryption is based on the mathematics of prime numbers. It transforms plain text into cipher text through a mathematical process, making the original data unreadable unless decrypted.
While tokenization swaps sensitive data with random tokens and keeps a link to the original data in a database. He says newer encryption models go beyond basic math, making modern encryption software even more secure for small businesses.
2. Tokenization struggles to scale, but encryption doesn’t
Encryption can handle large data volumes such as extensive customer databases or vast amounts of transaction data with a small encryption key to decrypt data. On the other hand, as data volume grows, tokenization becomes tough to scale securely due to the increasing size of the token database that needs to be managed and searched through. This impacts performance, making it better suited for small data chunks in low volume such as individual payment transactions or single user records.
Bodicherla suggests optimizing tokenization with the right system and network tweaks like having the tokenization system (the setup that manages the creation, storage, and mapping of tokens) close to the data source (the original sensitive data).
For larger or unstructured data such as big data analytics or video files, encryption is more scalable, but it requires all parties, like different departments or partner companies, to have keys. This can get complex and costly as more keys mean more management, distribution, and the potential for mishandling, especially if many parties are involved or change frequently. A good password management software should help here.
LastPass password management helps store and manage encryption keys (Source)
3. Tokenization is used for structured data fields only
Bodicherla explains that tokenization is specifically used for structured data fields like payment cards or social security numbers, where the data follows a predictable format. A predictable format means the data is organized in a way that's easy to anticipate, like having specific columns for name, date of birth, and account number in a database.
On the other hand, encryption is more versatile; it's used for both structured fields, such as customer databases, and unstructured data, such as entire files like audio or video files, where the data doesn't follow a fixed format.
This distinction allows businesses to choose the right method based on the type of data they handle, like customer information or multimedia files, ensuring better security against unauthorized access or data breaches and operational efficiency in managing and accessing the data.
4. Exchanging data is easier in encryption
Encryption is a more favorable choice when exchanging sensitive data, such as financial records, with third parties like partner companies, provided they have the encryption key. Unlike tokenization, which demands direct access to a token vault (a secure database that holds the original data and its corresponding tokens) for mapping token values (linking tokens to the original data) and can complicate data exchange of items like payment details, encryption facilitates this process as long as all involved parties have access to the keys.
In cases where they don’t, Bodicherla says key exchange algorithms like Diffie-Hellman (a method to share encryption keys over a public channel securely) or RSA (Rivest-Shamir-Adleman, a widely used encryption method) can be utilized. However, these can become costly if devices like smartphones or computers in the exchange keep changing.
Learn more about RSA (Rivest-Shamir-Adleman) and the other six encryption methods.
5. Tokenization doesn’t compromise security’s strength
Encryption, especially when using format-preserving schemes (methods that keep data’s original format even after encryption), often faces a trade-off of lower security strength due to the constraints imposed to maintain the format.
On the other hand, tokenization lets you keep the data format without reducing security strength. Bodicherla highlights strong tokenization systems like those used in payment processing, which mirror encryption's security features, like scrambling data, as good options.
He says these systems become particularly powerful if the storage area within the token system itself is encrypted, making it hard for unauthorized access. By opting for such setups, businesses can keep their data format intact while ensuring strong security.
Tokenization vs. hashing: What’s the difference?
Tokenization replaces sensitive data with non-sensitive substitutes, called tokens, while keeping the original data stored securely, for example, by swapping credit card numbers with random strings.
Hashing, however, changes data into a fixed size of characters using a hash function, making it impossible to revert to the original data.
Unlike tokenization, where the original data can be retrieved, hashing is a one-way process, making it ideal for verifying data integrity without revealing the actual data.
6. Tokenized data never leaves the organization
Typically, in encryption, the original data, though in encrypted form, can leave the organization. However, with tokenization, the norm is that the original data stays within the organization, meeting specific compliance standards such as the Payment Card Industry Data Security Standard (PCI DSS).
Yet, Bodicherla offers a different perspective. He states that whether tokenized data leaves the organization largely depends on the company's workflows. For instance, if a company shares tokenized data, such as payment information, with an external vendor like a payment processing company, the data can leave the organization, highlighting that the movement of tokenized data isn't as rigid as often perceived.
Unsure about choosing between encryption and tokenization? Ask these questions
It's common for small business owners to get confused between encryption and tokenization due to their technical natures. Bodicherla suggests small business owners think more about their use cases to decide the best security approach for their business and ask the following four questions:
1. Am I securing data for transmission/storage, or am I trying to mask data so I only expose parts of the data based on a need-to-know basis?
Data transmission means sending data from one place to another, and encryption can be a good choice to keep this data safe while it's being sent. If you're looking to hide some parts of your data and only show it to certain people who need to see it, tokenization might be the better choice.
2. How much data do I need to secure? Tokenization doesn’t scale beyond a certain point.
Knowing the amount of data you need to secure is important. Encryption can handle a lot of data, but tokenization can get slow if there's too much data. This question can help you decide which method is more practical for the amount of data you have.
3. Is my data structured? Or do I need to comb through large volumes of data? This has implications for scalability.
Structured data has a set format, like a database with names and addresses. Unstructured data is more random, like a bunch of different files. Knowing what kind of data you have helps decide which method, encryption or tokenization, is better suited for your data.
4. Can I use off-the-shelf components for implementing either? Or do I need to build custom components? Are there any regulatory requirements that necessitate either of these?
This question helps understand how easy it will be to implement encryption or tokenization. It also checks if there are any legal requirements you need to follow. Knowing this can help you decide which method fits better with your business setup and legal needs.
Once you are done pondering these questions with your team, use GetApp’s free strategy on a page template available for download below. This templatized scorecard can help you look at your strategy from a bird’s eye view to spot any errors and iron them out.
Note: The screenshots of applications included in this article are examples to show a feature in context and are not intended as endorsements or recommendations.
Methodologies
*GetApp’s IT Management Survey was conducted in June 2023 among 500 respondents to learn more about IT management practices at U.S. businesses. All respondents were screened for IT positions at companies with 1000 or fewer employees.
**GetApp's 2022 Data Security Survey survey was conducted in August 2022 among 1006 respondents who reported full-time employment. 289 respondents identified as their company's IT security manager.
***GetApp's 2023 Data Security Survey was conducted in August 2023 among 872 respondents to learn more about data security practices at U.S. businesses. All respondents were screened for full-time employment at U.S. businesses. 362 respondents identified as IT management professionals, and 271 identified as IT security managers.
Sources
Tokenization Guidelines, PCI Security Standards Council
Vikram Bodicherla, LinkedIn

Bhavya Aggarwal

